Networking, also known as computer networking, means that networked devices can share resources and exchange data or information. This is known as networking. A computer network is a group of linked computers that enables data exchange and communication between devices via a communication channel.
In prestigious firms like Cisco, Accenture, Uber, Airbnb, Google, Nvidia, Amazon, and many more, computer networking is the most frequently requested question. You must become proficient at answering networking interview questions if you want to be considered for employment at these and other IT product-based companies.
Label of content:
- Basic Networking Interview Question.
- Advanced Networking Interview Questions.
Basic Networking Interview Questions and Answers:
Q #1). How are network types classified?
Networks can be categorized according to their topology, size, function, technology, and other factors. Here are some typical classification schemes for networks:
By scope:
- Personal area network (PAN)
Devices within around ten meters of a person can be connected via a personal area network, or PAN. Bluetooth, for instance. - A local area network, or LAN, links devices in a certain geographic region, such as a house, workplace, school, etc.
Devices inside a city or metropolitan region are connected via a metropolitan area network, or MAN.
Wide-area networks, also known as WANs, connect devices dispersed over vast geographical regions or the entire globe.
In terms of topology:
- Bus topology: Every node in a bus architecture is linked to a single wire or path.
- Ring topology: A closed loop of nodes is formed, with each node connected to the one behind it.
By transmission medium:
- Wireless network: uses radio waves/microwaves for transmission. Examples: Wi-Fi, Bluetooth, and mobile networks.
- Wired network: uses physical cabling like Ethernet cables for transmission.
Q #2). Name two technologies with which you would connect two offices in remote locations.
Here are two common technologies that can be used to connect two offices located in remote locations:
- Wide Area Network (WAN): A WAN uses telecommunication networks and protocols to connect offices across broad geographic distances. Common WAN technologies include:
- MPLS (Multiprotocol Label Switching) is a specialized, private network that prioritizes corporate traffic, commonly utilized by enterprises.
- VPN (Virtual Private Network): Uses encryption to create secure “tunnels” through public networks like the Internet. Common protocols are IPsec and SSL VPNs.
- Leased lines are dedicated circuits leased from telecom providers that provide consistent bandwidth for connectivity. Options are T1, T3, fiber, etc.
- Internet Connection: The public internet can be used to connect remote offices through secure protocols.
- Internet broadband: technologies like DSL, cable modems, and fiber provide high-speed internet access.
- Cloud connectivity: Services like AWS Direct Connect and Azure ExpressRoute provide private connections to cloud platforms hosting business applications.
- SD-WAN (Software-Defined WAN) leverages multiple internet links and is overlayed with security and application policies. Provides flexibility and redundancy.
Q #3). What is a link?
In networking, a link refers to the connection or channel that allows two network nodes or devices to communicate with each other. Some key points about links:
- Physical link: refers to the physical transmission medium, like cables, fiber optics, wireless signals, etc., that connects the nodes. Examples include Ethernet cables, coaxial cables, and fiber-optic cables.
- A logical link refers to the logical connection between network layers or protocols that allows communication to occur. For example, a TCP connection is a logical link between two IP addresses.
- Link layer: The second layer (Layer 2) of the OSI model defines protocols for node-to-node communication like Ethernet, Wi-Fi, PPP, etc. Links operate at this layer.
- Link state: The operational status of a link—whether it is active/inactive, available/unavailable for communication. Link-state protocols monitor link states.
- Bandwidth: The maximum data transfer rate of the link in bits per second. Higher-bandwidth links allow faster communication.
- Duplex mode: whether the link allows simultaneous two-way communication (full duplex) or one-way at a time (half duplex).
- Uplink/Downlink: Terms used in wireless networks to refer to links between devices and the main access point/base station.
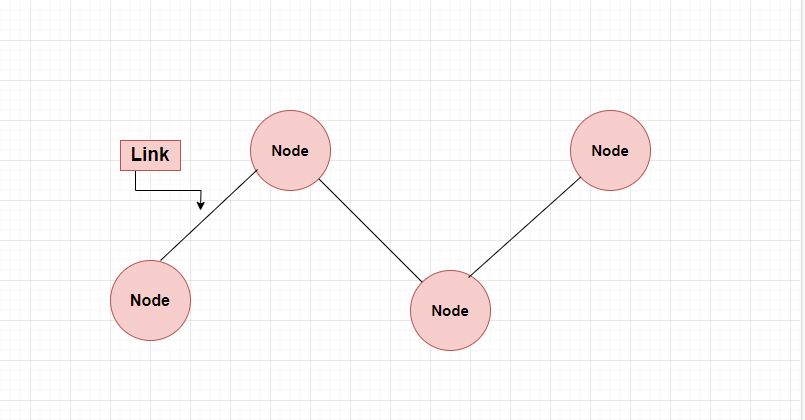
Q #4) What is a node?
Any device or endpoint that is a part of a network and can send, receive, or forward data to other nodes is referred to as a node.
Some essential node knowledge includes:
Computers, printers, switches, routers, IP phones, IP cameras, and other Internet of Things devices are examples of devices that can function as nodes. pretty much any gadget has a network interface.
Similar to an IP address for nodes in an IP network, nodes have a unique identifier on the network.
Node
What are the layers of the OSI reference model?
There are 7 OSI layers: 1) Physical Layer, 2) Data Link Layer, 3) Network Layer, 4) Transport Layer, 5) Session Layer, 6) Presentation Layer, and 7) Application Layer.
Name of the software layers in the OSI model.
- Application layer
- Presentation layer
- Session layer
Name the hardware layers in the OSI model.
- Network Layer
- Datalink layer
- physical layer
What are routers?
Routers are networking devices that forward data packets between several networks or subnets and link them together. Some essential router knowledge is as follows:
Data packets are meant to be sent between networks based on their IP addresses. In the OSI model, they function at layer 3, or the network layer. To determine which way to forward packets based on their destination IP addresses, maintain routing tables. Updates to tables are made via routing protocols.
Routing protocols like BGP, OSPF, and RIP are widely used. When a network changes, it assists routers in dynamically learning routes.

Routers have at least two network interfaces – one for each network they interconnect. Large routers have multiple ports.
What benefits does using a VPN offer?
- A few benefits of using a VPN are listed below:
VPN is less expensive than WAN connections and is used to remotely connect offices located in various regions.
VPN enables private data transfers and secure transactions between multiple offices located in different regions.
VPN uses virtualization to protect an organization’s data from potential attacks and breaches.
A VPN masks one’s online identity and encrypts internet traffic. - Routing protocols like BGP, OSPF, and RIP are widely used. When a network changes, it assists routers in dynamically learning routes.
Name some services provided by the application layer in the Internet model?
Some services provided by the application layer in the Internet model are as follows:
- Mail services
- Directory services
- File transfer
- Access management
- Network virtual terminal
What is anonymous FTP?
An anonymous file transfer protocol (FTP) allows users to access files on public servers. Users who are granted access to these servers’ data do not have to provide their identity; instead, they can log in as anonymous visitors.
What is the difference between a hub, switch, and router?
Hub:
- Operates at the physical layer (layer 1) of the OSI model.
- Connects multiple devices using a shared medium.
- Acts as a repeater and retransmits all data to all ports.
- It is not very scalable and has a low bandwidth.
- It doesn’t support collision domains and is only half duplex.
Switch:
- Operates at the data link layer (layer 2) of the OSI model.
- Connects multiple devices and segments the network.
- Learns the MAC addresses of devices and switches packets accordingly.
- Increases bandwidth by establishing separate collision domains.
- Full duplex for increased performance.
- It’s more scalable than hubs.
Router:
- Operates at the network layer (layer 3) of the OSI model.
- Connects multiple networks or subnets.
- Uses IP addresses to forward packets to the correct network.
- Maintains routing tables to determine paths.
- Establishes separate broadcast domains for security.
- Supports routing protocols to dynamically learn routes.
- Scalable, high-performance device for larger networks.
What is a subnet mask?
A subnet mask is a 32-bit value that is used to separate the host and network portions of an IP address. Important details regarding subnet masks:
To properly organize IP addresses, subnet masks enable the establishment of subnets inside a classful network.
Dotted decimal notation, such as 255.255.255.0 or 255.255.0.0, is used to express it. The number of 1s in the mask determines the network and host components of the IP.
The bits in the mask set to 1 represent the network portion of the IP address. Bits set to 0 indicate the host portion.
For example, the first three octets (24 bits) of a mask of 255.255.255.0 represent the network, and the last octet (8 bits) represents the host.
What is firewall?
Using pre-established security rules, a firewall is a type of network security system that keeps an eye on and regulates both incoming and outgoing network traffic. Important facts concerning firewalls:
situated at a network’s edge to defend internal resources from outside threats.
filters data flowing between an untrusted external network, such as the Internet, and an internal network.
Filters are based on IP addresses and ports and operate at Layer 4, or the transport layer, of the OSI model.
Common types of firewalls include next-generation firewalls, software/virtual firewalls, and hardware/physical firewalls.
Explain the TCP/IP model.?
TCP/IP, or Transmission Control Protocol and Internet Protocol, is the most commonly used and accessible protocol. In its end-to-end data communication, TCP/IP specifies how data should be packaged, transported, and routed.
List the three user authentication methods.
A password, token, or biometric (such as an iris scan or thumbprint) are examples. Additionally, two-level authentication makes use of those two techniques.